Reveal high-risk exposures on internet-facing assets that require remediation to protect against data breaches, fines and downtime.
Risk-Based Vulnerability Management
Prioritize the vulnerabilities that pose you the most risk.
Reveal high-risk exposures on internet-facing assets that require remediation to protect against data breaches, fines and downtime.
Unlock visibility of every internet-facing asset and associated exposure across your organization’s attack surface. Agentless monitoring uncovers assets that evade detection by traditional discovery tools, as well as those not normally monitored by security teams — think misconfigured Amazon S3 buckets and forgotten marketing websites.
Additionally, Ivanti Neurons for EASM monitors continuously to ensure near-real-time visibility of assets, so you know right away when existing assets become exposed or new assets are deployed and can respond accordingly.
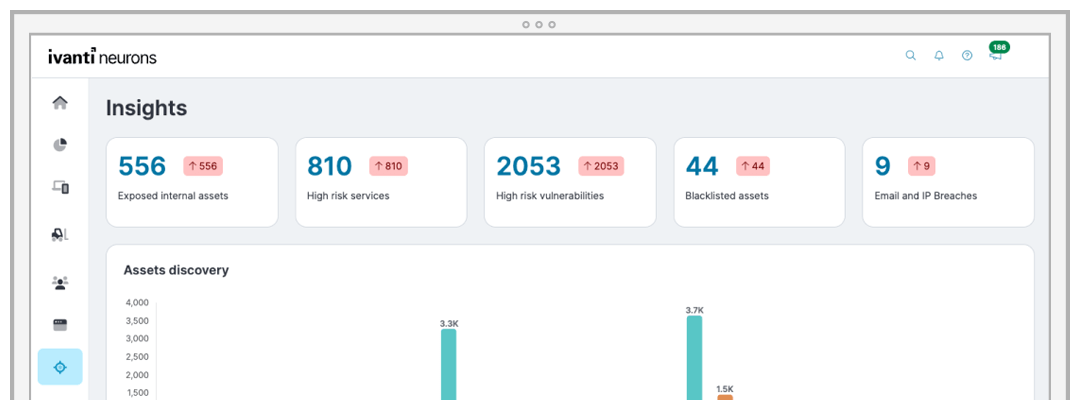
Unlock visibility of every internet-facing asset and associated exposure across your organization’s attack surface. Agentless monitoring uncovers assets that evade detection by traditional discovery tools, as well as those not normally monitored by security teams — think overlooked QA environments and forgotten marketing websites.
Additionally, Ivanti Neurons for EASM monitors continuously to ensure near-real-time visibility of assets, so you know right away when existing assets become exposed or new assets are deployed and can respond accordingly.

Leverage actionable intelligence on exposures across your external attack surface to determine where to direct remediation efforts.
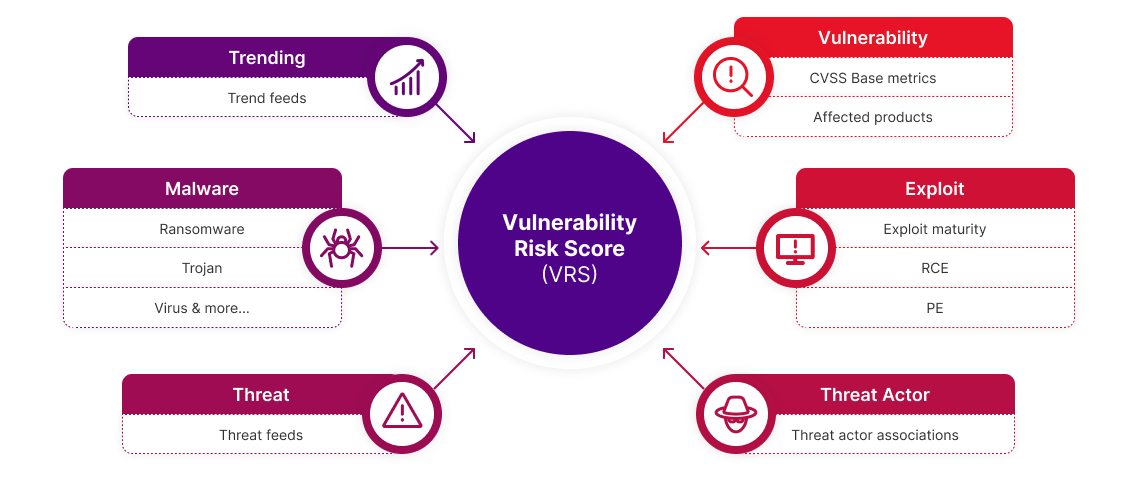
Intelligence includes a Vulnerability Risk Score (VRS) for every CVE that Ivanti Neurons for EASM finds. VRS empowers informed decision-making by enabling security teams to quantify the risk posed by a vulnerability and understand its threat context.

Satisfy reporting requirements from senior-level security stakeholders and aid in due diligence on potential acquisitions, partners and vendors with PDF reports. These exportable reports provide a thorough rundown of the exposures associated with an organization’s external attack surface.

Tap into the power of Ivanti Neurons to close critical attack surface gaps unearthed by Ivanti Neurons for EASM. Couple Ivanti Neurons for EASM with the following products to enable the fastest response to issues impacting external-facing assets:

Each vulnerability identified by Ivanti Neurons for EASM is assigned a Vulnerability Risk Score (VRS) that’s defined by aggregating a range of attributes that reflect the impact of a vulnerability in a given environment.
Ivanti offers a range of other risk-based solutions.
Questions? Contact our team.